When leaders and IT teams ask me about alternatives to Microsoft 365, the conversation usually starts with flexibility. Modern work is no longer limited to one toolset or one fixed way of collaborating. Different teams work differently, and the tools they use should support that reality. From my experience, many organizations start exploring alternatives when […]
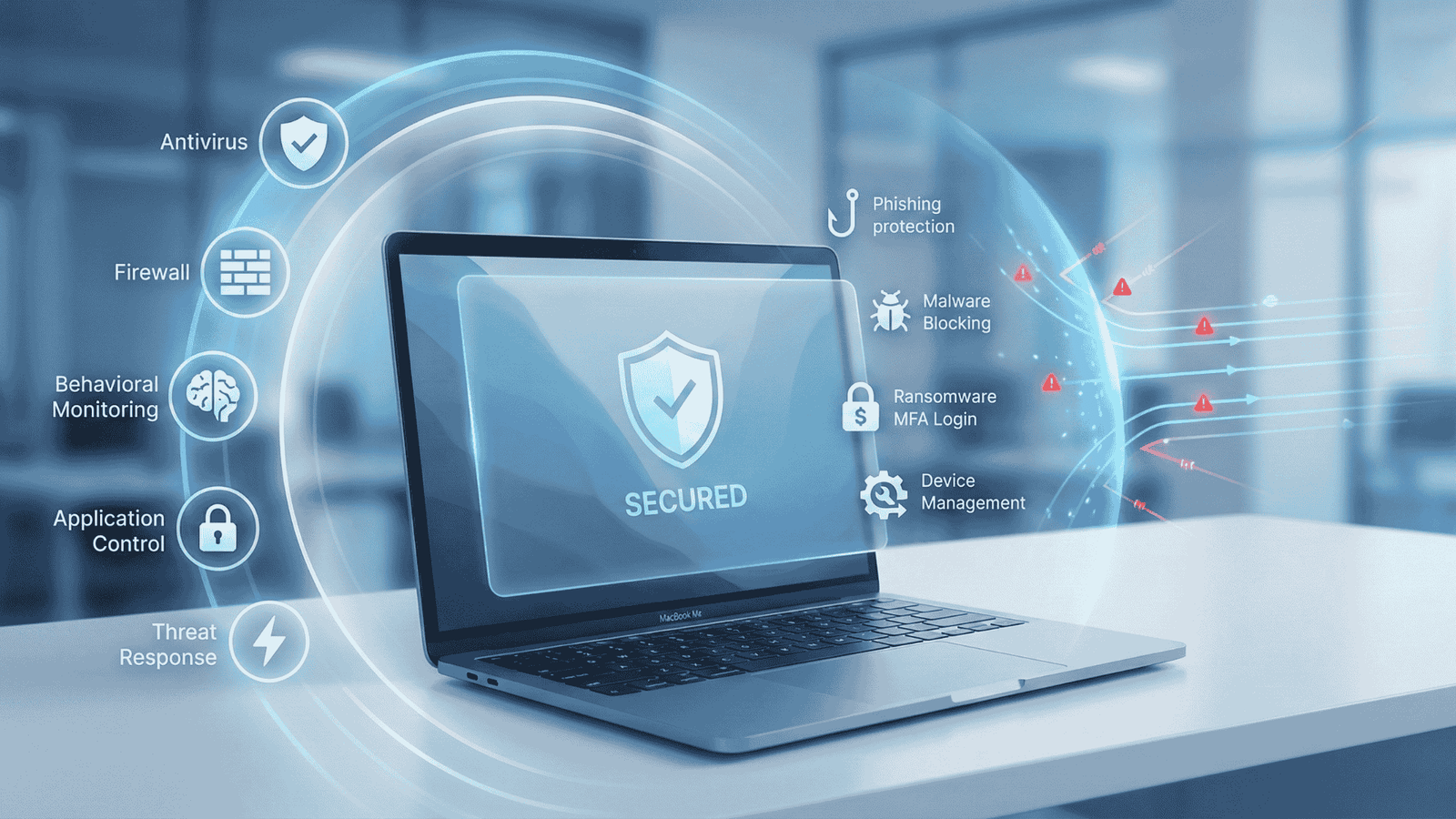
Introduction to Endpoint Security for Mac When people talk about cybersecurity, Mac devices are often assumed to be safer by default. In my experience, that assumption creates more risk than protection. Mac endpoints are now widely used in enterprises, remote teams, and leadership roles, making them a prime target for modern attacks. This is where […]
When business leaders ask me how long does cloud migration take, my honest answer is always it depends. In enterprise environments, cloud migration is not a single task. It is a structured transformation that impacts infrastructure, applications, security, and operations. In my experience, organizations that first understand the different types of cloud migration approaches move […]
In my experience working with organizations adopting Microsoft 365, one question keeps coming up again and again. Is Microsoft Access part of Office 365, and does it still make sense to rely on it in a cloud first environment? The confusion is understandable. Microsoft 365 has evolved rapidly, focusing more on cloud services, browser based […]
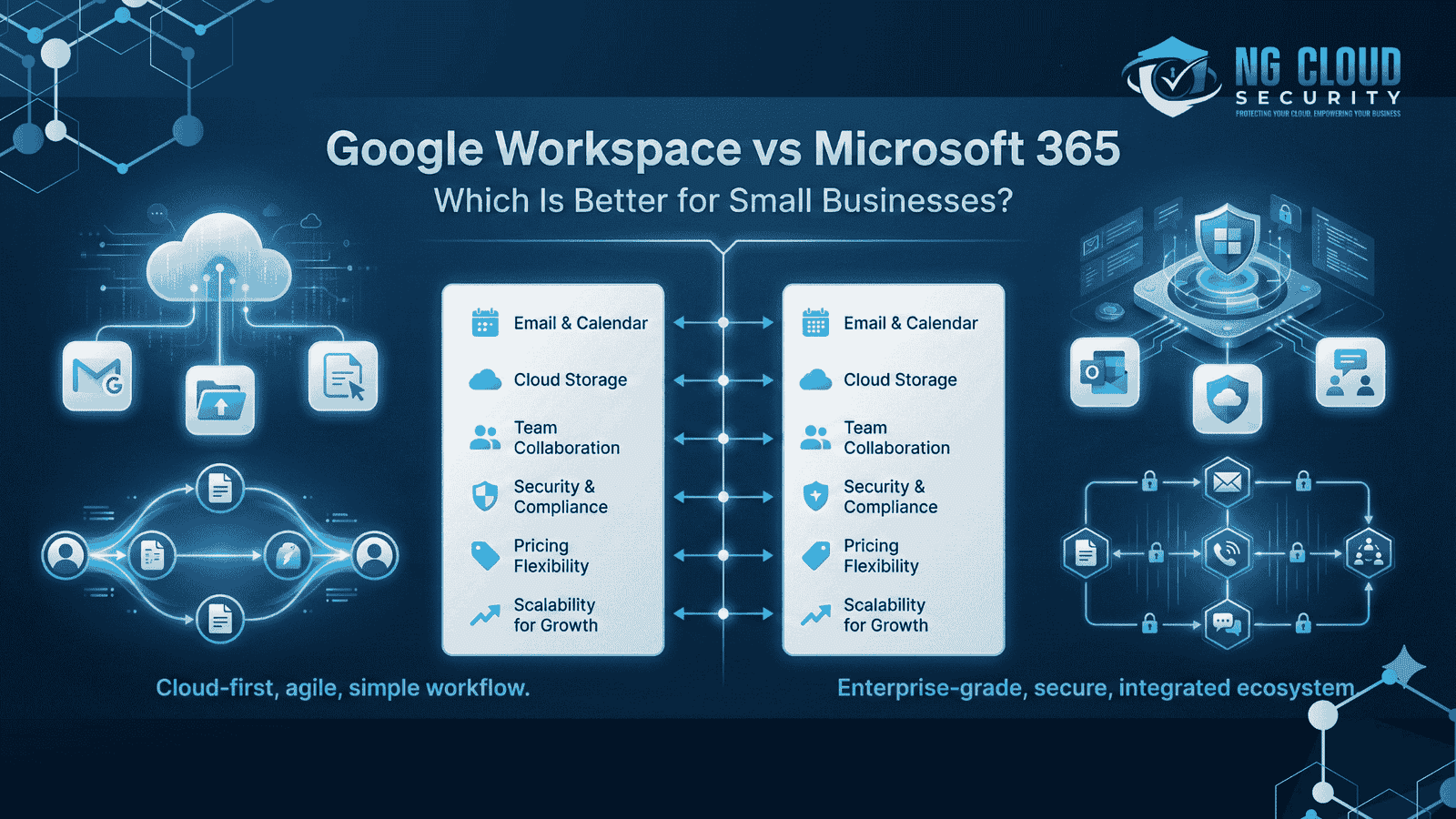
When small business owners ask me to compare productivity platforms, the discussion usually comes down to google workspace vs microsoft 365 for small business. I have seen both platforms used across different industries, and the right choice often depends on how a business works today and how it plans to grow. Productivity tools are no […]
One of the most common questions I hear from business owners today is simple but important. How does zero trust work and why is it becoming the foundation of modern cybersecurity. From my experience working with organizations moving to cloud and hybrid environments, traditional security models no longer match how businesses actually operate. Users work […]
Over the last few years, I have seen a major shift in how organizations think about remote access security. As cloud adoption grows and workforces become more distributed, the conversation around zero trust network access vs vpn has become more important than ever. In 2026, security teams are no longer asking which solution is easier […]
Modern businesses are expected to move fast, stay secure, and support flexible work environments. In my experience, many organizations struggle not because of people or processes, but because their digital tools do not work together. This is where Microsoft 365 creates real impact. When used correctly, the benefits of Microsoft 365 go far beyond email […]
Introduction to Types of Cloud Migration In my experience working with growing businesses and large enterprises, cloud migration almost always starts with confusion. Everyone knows they need the cloud, but very few are clear about the different types of cloud migration and how each one impacts security, cost, and long term scalability. Cloud migration is […]
Article Summary / Key Takeaways: This article explains how IT admins can use Windows Hello for Business with the Cloud Kerberos Trust model to achieve true passwordless sign-in for hybrid environments. This method eliminates the need for a complex and costly on-premises Public Key Infrastructure (PKI), allowing users to access both cloud and on-prem resources […]